Blog
Share this
7 ERP Security Best Practices to Protect Your Business

by Jalene Ippolito on August 18, 2022
Your ERP system is the center of your business, housing mission-critical data across all areas of your business. With the average number of cyber attacks per company increasing by 32% in 2021, protecting that data from outside threats is more important than ever.
For SMEs (small to mid-size enterprises), staying on top of the latest threats and properly securing your ERP system can be a real challenge. Chances are you don’t have resources dedicated to IT security the way larger organizations do. And many IT professionals lack expertise in ERP security. Ultimately this leaves smaller organizations vulnerable to cyber attacks – according to research from Cybersecurity Magazine, 43% of all data breaches involve SMEs.
Whether you're going through an ERP implementation or you've been live for a while, we recommend starting with these ERP security best practices to minimize your risk.
Why ERP security matters
If even one piece of your ERP system is compromised, your most valuable data across the entire business can potentially be exposed. This can have a significant impact on your business including:
- Interruption to your business operations (and the hard cost associated with downtime)
- Cost to recover your data and repair system security
- Restoration costs if your data is altered, damaged or lost
- Loss of trust and damage to your brand’s reputation if customer data is compromised
While the risk is clear, properly securing your ERP system is complex. You’re dealing with security for infrastructure, networks, operating systems, integration points and the database itself. This is why SMEs tend to be more vulnerable – general-purpose security measures don’t cut it. You need people who understand the ERP database, cloud platforms and web services (like your ERP partner).
How to protect your ERP system
A quick note on deployment models before we dive into best practices. With a cloud solution (private or public), security is a shared responsibility between your company and your cloud provider. This is what the split typically looks like but talk with your provider to make sure you’re both clear on your responsibilities.
You’ll handle the human side of things – enforcing password policies, training staff on security protocols, managing user authorizations and installing regular updates.
And your cloud provider will look after the following:
- Physical security of their data centers
- Continuity and backup best practices
- Redundancy to protect against ransomware attacks
- Data encryption
- Multi-factor authentication
- System monitoring
If you run an on-premise ERP solution, you’ll be responsible for all security measures, backups, data restoration and system monitoring. Few SMEs have the internal resources to manage this properly, which is why many are moving to a private cloud option.
1. Understand where your vulnerabilities are
Having a clear picture of your ERP landscape will help you identify potential weak spots that need attention. Consider all elements of your ERP system including processes, master data, infrastructure, storage networks, interfaces and integration points with other applications.
Once you’ve identified potential vulnerabilities, assess the implications of a hack.
- Would an attack bring down the entire system?
- Is the impact minimal (e.g. a small delay in invoicing) or will it result in lost revenue?
If you integrate with other best-of-breed applications, make sure you understand how they’re secured. Do they use multi-factor authentication (MFA)? Is the data encrypted? Does the vendor provide system monitoring?
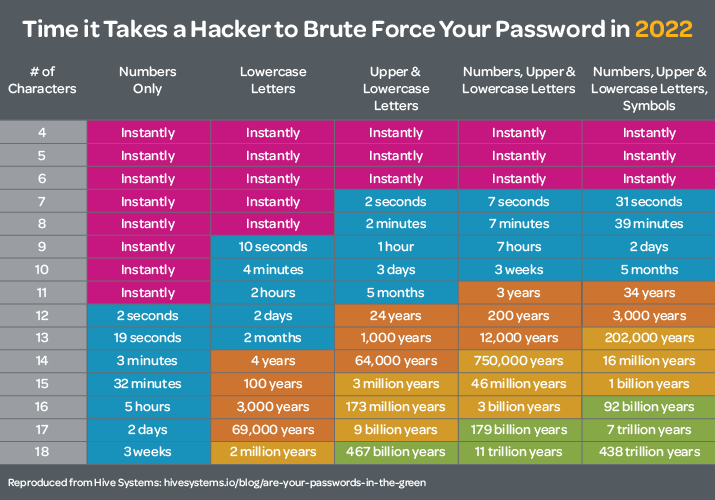
2. Enforce strong password policies
Let’s say you have a 5-character password with a combination of numbers, upper/lowercase letters and symbols – how long do you think it takes a hacker to get your password?
According to Hive Systems – instantly.
The days of using your favorite go-to password for every account (qwerty123 anyone?) are long gone.
As much as your team might find it annoying, setting complex password policies and enforcing regular password changes is essential to ERP security. Here are the latest recommendations from Cyber News:
- At least 12 characters long
- A mix of upper and lowercase letters, numbers and special symbols
- Doesn’t contain memorable keyboard paths
- Isn’t based on personal information
- Password is unique for each account
To make it easier for your team to manage all their complex passwords, consider rolling out a password manager like Dashlane. These tools allow you to randomly generate strong passwords, store them securely and monitor for duplicate passwords or potential breaches.
3. Implement multi-factor authentication
Multi-factor authentication is becoming the norm for web applications – you likely use it for your banking and even Facebook. Yet over 40% of companies still don’t use MFA on all potential ERP entry points.
On top of those strong passwords, MFA gives you an added layer of protection by asking users to confirm their identity through either a text or an app like Duo. For public cloud ERP software, like NetSuite, two-factor authentication is typically triggered right from the webpage where you login. If you’re running your ERP system on-premise or in a private cloud, you can attach a multi-factor authentication procedure to the remote desktop or remote app login.
4. Stay on top of updates
Outdated software can present an increased security risk. Whether it’s your on-premise ERP software, Windows operating system or another application that interfaces with your ERP, create a policy to implement updates regularly. With public cloud software, the vendor typically performs upgrades automatically, giving you access to the latest security patches.
5. Use proper authorizations
The rule of thumb for user authorizations is to only give people access to the information and functionality they need to do their jobs – and nothing more.
For your ERP software, this should be strictly followed. Do a user audit to understand what roles you have and the permissions they currently have. If they have more than they need, adjust authorizations as needed, then document your policies. You’ll also want to review employee access anytime there’s a role change within the organization to ensure their authorizations still reflect the requirements of their job. And finally, add an item to your employee departure checklist to make sure user accounts for your ERP system and any integrated software are deactivated when someone leaves your company.
6. Continually educate your team
Most cybersecurity issues are the result of human error. Someone unwittingly clicks the link to a fake invoice (not noticing the sketchy email address) and suddenly your network is at risk.
Given how quickly cyber threats are evolving, training your team isn’t a one-and-done event. You need to provide ongoing education to ensure everyone understands your policies and their role in protecting your systems. Your IT team should dedicate time to staying current on the constantly changing threat landscape and adjusting your security practices as needed.
For your larger team, focus training on:
- Password policies
- How to spot phishing attempts
- Internal security protocols
- What to do when an event occurs
Training requires a time investment but remember that human error is your top vulnerability and well-trained people make fewer errors.
7. Create an incident response plan
Even with all the right security measures in place, you want to be prepared for an incident before it happens. That’s where your incident response plan comes in to help you detect security events and take the appropriate steps to solve the issue.
Your plan should include:
- An overview of the high-level goals, scope and assumptions
- An outline of the roles and responsibilities (for your team and your cloud provider)
- A detailed list of incidents that require action, including specific threats and situations that require formal incident response actions (e.g. denial of service attacks, malware infections, email phishing, lost/stolen laptops)
- Detection and containment procedures, including notifying team members and outside parties, securing your network, confirming the incident, gathering evidence and reporting findings
- Eradication steps to clean up the incident, such as analyzing network traffic and system logs, and confirming resolution through vulnerability testing
- The recovery phase where you reinstall hosts, reset passwords, adjust firewall rules, etc.
- When and how to alert those impacted by a confirmed breach (as required by contract or law)
Final thoughts
Nothing in life is guaranteed. So, when it comes to your mission-critical systems and data, you plan for the worst and hope for the best. Implementing these ERP security best practices will help you do just that.
If you’re searching for new ERP software and want to chat about the security implications of cloud versus on-premise ERP (or public versus private cloud), reach out to us. Our team is here to help.
Share this
Stay in the Know!
Join other SMEs who receive our monthly ERP insights, tips and best practices.
You may also like

ERP Funding for Canadian Businesses

Should You Work with a NetSuite Implementation Partner or Go Direct?